CyberSecurity Standards

IT Security Standards Kit
What are important IT security standards? What are useful ways to implement cyber security and how to prepare for a Cybersecurity Audit according IEC, NIST, ISO27001:2013 standards? Download this IT CyberSecurity Kit? Download this IT standards kit now.
- IT Security Gap analysis
- IT Security Audit Checklist
- Data Backup Plan
- Data Security
- Security Incident Management
- Vulnerability Management
- User Access
- Logging and Monitoring
- Cloud Computing Security
- IT Asset Management
- Change Management
- IT System Acquisition & Development
- Web Application Security
- Physical Security
- Bring Your Own Device BYOD
- End-User Protection
- Network Security
- IT Recovery
- Information Security Risk & Compliance Management
- Human Resources Security
- IT Acceptable Use
- Third-Party Risk Management
- Secure Algorithm List
- Data Classification Standard
- Etc
IT Security Roadmap
How to implement CyberSecurity in your organization? What are the ways to implement cyber security? Download this IT Standards Roadmap if you are working on IEC, NIST, ISO27001:2013 or other control objectiv
IT Infrastructure Director Resume
How to create an IT Infrastructure Director Resume? Download this IT Infrastructure Director Resume template now!
Cyber Security Incident Report template
How to create a professional Cyber Security Incident Report? Download this Cyber Security Incident Report template now!
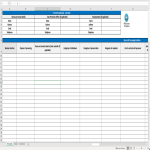
IT Service Level Agreement
How to create an IT Service Level Agreement? Download this It Service Level Agreement template now!
GDPR Data protection policy
Are you looking for this GDPR Data protection policy sample? Is your organization GDPR ready? Download this GDPR Data protection policy now
Security Audit Checklist
How to perform a professional Security Audit? How to create a Security Audit Checklist? Download this Security Audit Checklist template now!
IT Security Policy Government Example
How to draft a Policy for the IT Security of your organization? An easy way to start implementing IT Security is to download this Information Security Policy te
Security Risk Management Plan
Are you looking for a professional Security Risk Management Plan? Download this Security Risk Management Plan if you are working on IEC, NIST, ISO27001:2013
Security Threat Assessment
How to create a Security Threat Assessment? Download this Security Threat Assessment template now!
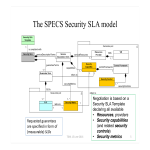
Security Service Level Agreement Template
How to create a Security SLA? Download this Security Service Level Agreement template that will perfectly suit your needs!
IT Security Training Policy
How to create an IT Security Awareness Training Policy for your organization? Download this government IT Security Training Policy if you are working on IEC, NI
Security Incident Report
Are you looking for a professional Security Incident Report? If you've been feeling stuck or lack motivation, download this template now!
HIPAA Security Incident Report
How to create a Hipaa Security Incident Report? Download this Hipaa Security Incident Report if you are working on IEC, NIST, ISO27001:2013 or other IT and Cybe
GDPR Supplier Data Processing Agreement
Are you looking for this Supplier Data Processing Agreement? Download this Supplier Data Processing Agreement now!
IT Security Roadmap
How to implement CyberSecurity in your organization? What are the ways to implement cyber security? Download this IT Standards Roadmap if you are working on IEC, NIST, ISO27001:2013 or other control objectiv
IT Security Standards Kit
What are important IT security standards? What are useful ways to implement cyber security and how to prepare for a Cybersecurity Audit according IEC, NIST, ISO27001:2013 standards? Download this IT CyberSecurity Kit? Download this IT standards kit now.
Data Security Plan
How to create a Data Security system? Download this Data Security plan if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and control o
Data Classification Standard
How to create a Classification Standard for the data in your organization? Download this Data Classification Standard if you are working on IT cybersecurity sta
IT Security Disaster Plan
How to create an IT Security Disaster Plan? Download this IT Security Disaster Plan if you are working on IEC, NIST, ISO27001:2013 certification.
IT Security Compliance Project Charter
How to write a Project Charter for an IT Security Standards implementation project? Check below for the details and download the Project Charter IT Security Standards implementation template
IT Security Documentation Controller
How to create a Documentation Controller for IT Security project? Download this Documentation Controller if you are working on IEC, NIST, ISO27001:2013 or other
ISO27001 Internal Audit Checklist
How to perform an Internal Audit for compliance with IT security standards? Download this Iso 27001 Internal Audit Checklist if you comply with CyberSecurity.
Internal IT Security Gap Analysis
How to do an internal analysis of the IT Security status of your organization? Download this Internal IT Security Gap Analysis
IT User Access Policy
How to create a User Access Policy for the management of IT in a company? Download this IT User Access Policy if you are working on ISO27001, NIST, IEC or any o
Web Application Security Standard
How to write a Web Application Security Standard for IT organization? Download this Web Application Security Standard if you are working on NIST, ISO27001 or an
Logging and Monitoring IT Standard
Download this Logging and Monitoring IT Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and control objectives.
IT Recovery Standard
How to create an IT Recovery Standard for your organization? Download this IT Recovery Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and C
End User Protection IT Standard
How to write an End-User Protection Standard? Download this End User Protection IT Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber
Vulnerability Management IT Security Standard
How to create a Vulnerability Management IT Security Standard for your company? Download this Vulnerability Management CyberSecurity standard now.
Cloud Computing IT Security Standard
Download this Cloud Computing CyberSecurity Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and control objecti
Data Backup Plan
How to create a Data Backup Plan to improve your IT Security? Download this Data Backup Plan Standard if you are working on IEC, NIST, ISO27001:2013 or other IT
Security Incident Management IT Standard
How to create a Security Incident Management Standard for your IT organization? Download this Security Incident Management if you are working on IEC, NIST, ISO2
IT Asset Management Cybersecurity Standard
How to create an IT Asset Management System for your organization? Download this IT Asset Management Standard if you are working on IEC, NIST, ISO27001:2013, or
Change Management IT Cybersecurity Standard
How to create a Change Management CyberSecurity standard for your organization? Download this IT Security Standard now Standards and control objectives
IT System Acquisition & Development
How to create an IT System Acquisition & Development Standard? Download this IT System Acquisition Standard if you are working on IEC, NIST, ISO27001:2013, etc
Physical Security IT Standard
How to create a Physical Security Standard for IT Assets? Download this Physical IT Security if you are working on IEC, NIST, ISO27001:2013, or other IT and Cyb
Network Security IT Standard
Download this Cybersecurity standard for Network Security if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and controls
IT Security Risk & Compliance Management
How to create an Information Security Risk and Compliance Management Standard? Download this IT Information Security Risk & Compliance Management Standard now.
Human Resources IT Cybersecurity Standard
How to create a Human Resources IT Cybersecurity Standard for your company? Download this HR IT Security Standard model if you are working on IEC, NIST, ISO2700
Third Party Risk Management Standard
How to create a Third-Party Risk Management Standard for your IT organization? Download this Third-Party Risk Management if you are working on IEC, NIST, ISO270
Secure Algorithm List IT Security Standard
How to create a Secure Algorithm List for IT organization? Download this Secure Algorithm List if you are working on IEC, NIST, ISO27001:2013 cybersecurity.
Acceptable Use IT CyberSecurity Standard
How to define an Acceptable Use IT CyberSecurity Standard? Download this Acceptable Use IT Security Standard template if you are working on IEC, NIST, ISO27001:
Employee Confidentiality Statement IT Security
How do you write a confidential statement? Download this Employee Confidentiality Statement if you are working on NIST, Cyber Essentials (UK), ISO/IEC 27001:201
Statement Of Applicability CyberSecurity
How to create a Statement Of Applicability according CyberSecurity standards? Download this Statement Of Applicability if you are working on IEC, NIST, ISO27001:2013 or other IT and CyberSecurit
CyberSecurity Analyst Job Description
What is a CyberSecurity Analyst? Are you looking for a CyberSecurity Analyst Job Description? What are the important details in a CyberSecurity Analyst Job Desc