Security Service Level Agreement Template
Save, fill-In The Blanks, Print, Done!

Download Security Service Level Agreement Template
Adobe Acrobat (.pdf)- This Document Has Been Certified by a Professional
- 100% customizable
- This is a digital download (875.8 kB)
- Language: English
- We recommend downloading this file onto your computer.
How to create a Security SLA? Download this Security Service Level Agreement template that will perfectly suit your needs! Download this Security SLA if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and control objectives.
Legal professionals are in need of templates more than any other industry. Our trustworthy legal templates are all drafted and screened by legal professionals that have experience in special law-related fields and are actively involved in legal issues around the topic. This Security Service Level AgreemenTpresentatoin covers the most important subjects and will help you to structure and communicate in a professional and legal way with those involved.
Appropriate data security controls reduce the likelihood (and impact) of data breach incidents during various phases of the data lifecycle. The purpose of this standard is to set out the rules for securing the companies' data during transmission and storage. This document provides best practice recommendations on information security management for use by those responsible for initiating, implementing or maintaining information security management systems (ISMS).
Nowadays, with the digitalization of our society, the need for data protection became more important. The latest IT Security Standards involve the application of technology to broader social and institutional contexts, and thereby contributes to the servitization of companies, and affects how they compete and interact. This document contains security technology solutions to protect data classified as “Highly Sensitive”, “Sensitive”, “Private” or “Public” as per the Data Classification Standard and Data Handling Guidelines. Specifically:
- Cryptography – Encryption and hashing solutions for protecting sensitive data when in transit or storage, and
- Data Masking – Data masking is a technology for obscuring sensitive information in non-production environments. Through data masking [Company Name] protects the content of sensitive data in non-production environments to ensure that:
- Application developers, testers, privileged users and outsourcing vendors do not have unauthorized access to such information.
- The data maintains the referential integrity of the original production data.
Using this PDF will help you to deal with the situation! However, this Legal template will help you dealing with this legal matter, we still recommend you to consider to find legal support in case you have doubts dealing with it the right way.
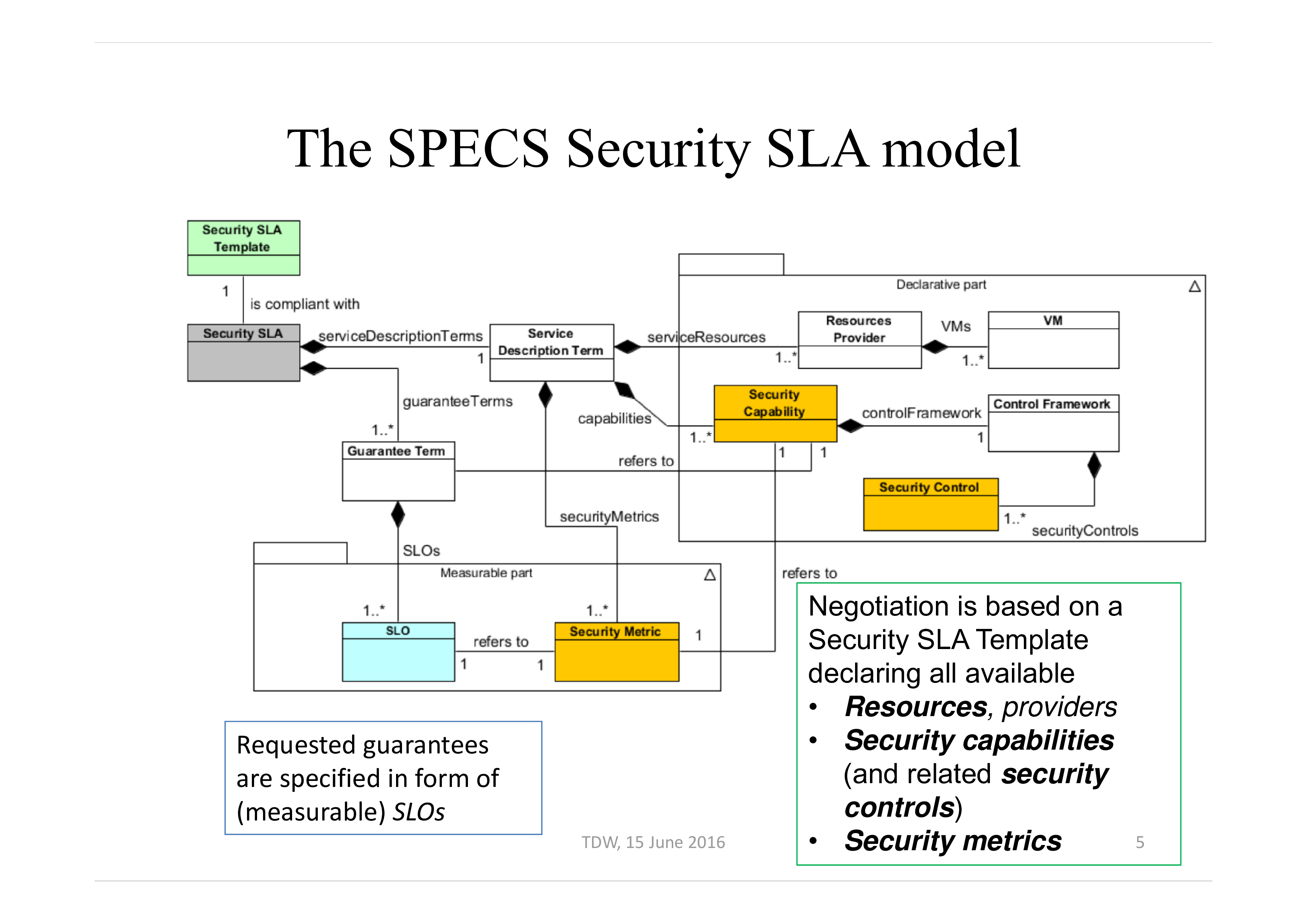
SLA’s Security From SLA to Security SLA TDW, The SPECS Security SLA model Requested guarantees are specified in form of (measurable) SLOs TDW, Negotiation is based on a Security SLA Template declaring all available
• Resources, providers
• Security capabilities (and related security controls)
• Security metrics 5 Security SLA life cycle Negotiate Implement Monitor Remediate Renegotiate • Agree on Security Controls and Metrics
• Activate Security Mechanism
• Collect Security Metrics measurement
• Identify Violations and apply remedies
• Change SLA terms TDW, Main concepts behind SLA negotiation
• Security SLA are modeled to cope with the semantic gap between not-expert customers and the needed standard technical controls that must be implemented to offer specific security capabilities The SLA model is compliant with available and on-going standards Research challenges: • The negotiation process must identify feasible offers to the customer
• The feasibility is evaluated according to security and CSP constraints • The offers are evaluated according to the security level they provide TDW, 15 June 2016 7 Main concepts behind SLA enforcement/remediation
• Dynamically add security to services even when services are provided by external CSP – Acquire and configure resources:
SLA-based acquisition of resources and enforcement of security mechanisms
• Research challenges: a quantitative approach to modular security to improve the security of services/resources offered by External CSPs – Resource provision in a multi-cloud environment – Transparent adaptation of security services Main concepts behind SLA monitoring
• Monitoring SLAs of services offered by external CSPs – Drive monitoring using SLAs – Notify possible SLA violations – Avoid violations with proactive reactions
• Research challenges: – Adapt monitoring to SLAs – Continuously monitor the security of services offered by external CSPs – Measure the
Download this Security SLA now. Besides this document, make sure to have a look at the IT Security Roadmap for proper implementation and this fit-for-purpose IT Security Kit here with over 40 useful templates. The document(s) are easy to modify and can be downloaded directly after purchase.
Also interested in other Legal templates? AllBusinessTemplates is the #1 source for Legal templates! Just search on our website and have instant access to thousands of free and premium legal agreements, contract, documents, forms, letters, etc used on a daily basis by professionals in your industry.
DISCLAIMER
Nothing on this site shall be considered legal advice and no attorney-client relationship is established.
Leave a Reply. If you have any questions or remarks, feel free to post them below.
IT Security Standards Kit
What are IT Security Standards? Check out our collection of this newly updated IT Security Kit Standard templates, including policies, controls, processes, checklists, procedures and other documents.
Read moreRelated templates
Latest templates
Latest topics
- GDPR Compliance Templates
What do you need to become GDPR compliant? Are you looking for useful GDPR document templates to make you compliant? All these compliance documents will be available to download instantly... - Google Docs Templates
How to create documents in Google Docs? We provide Google Docs compatible template and these are the reasons why it's useful to work with Google Docs... - IT Security Standards Kit
What are IT Security Standards? Check out our collection of this newly updated IT Security Kit Standard templates, including policies, controls, processes, checklists, procedures and other documents. - Letter Format
How to format a letter? Here is a brief overview of common letter formats and templates in USA and UK and get inspirited immediately! - Google Sheets Templates
How to work with Google Sheets templates? Where to download useful Google Sheets templates? Check out our samples here.
cheese