It Risk Assessment Report
Save, fill-In The Blanks, Print, Done!
Download It Risk Assessment Report
Adobe Acrobat (.pdf)- This Document Has Been Certified by a Professional
- 100% customizable
- This is a digital download (174.67 kB)
- Language: English
- We recommend downloading this file onto your computer.
How to draft a It Risk Assessment Report? An easy way to start completing your document is to download this It Risk Assessment Report template now!
Every day brings new projects, emails, documents, and task lists, and often it is not that different from the work you have done before. Many of our day-to-day tasks are similar to something we have done before. Don't reinvent the wheel every time you start to work on something new!
Instead, we provide this standardized It Risk Assessment Report template with text and formatting as a starting point to help professionalize the way you are working. Our private, business and legal document templates are regularly screened by professionals. If time or quality is of the essence, this ready-made template can help you to save time and to focus on the topics that really matter!
Using this document template guarantees you will save time, cost and efforts! It comes in Microsoft Office format, is ready to be tailored to your personal needs. Completing your document has never been easier!
Download this It Risk Assessment Report template now for your own benefit!
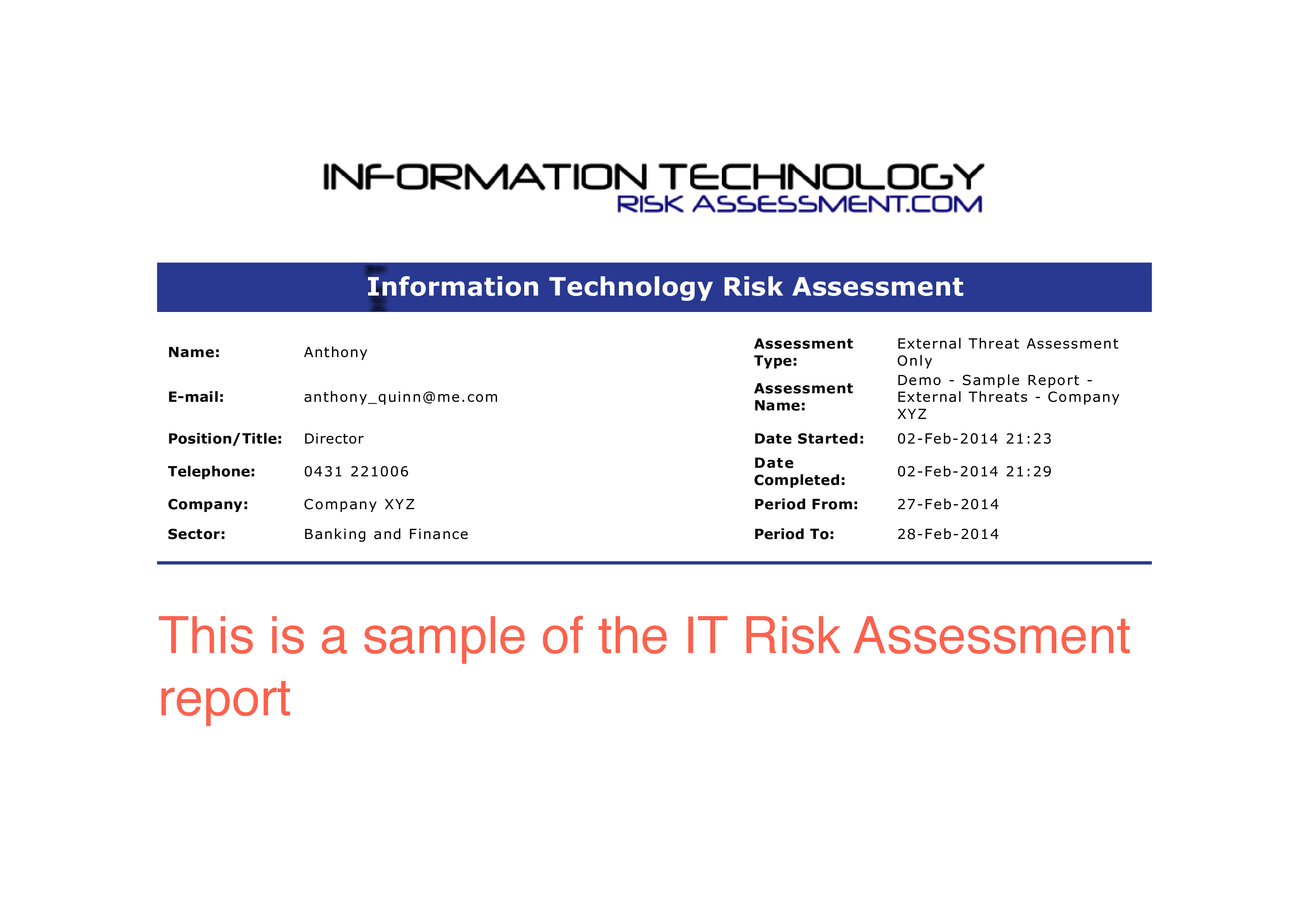
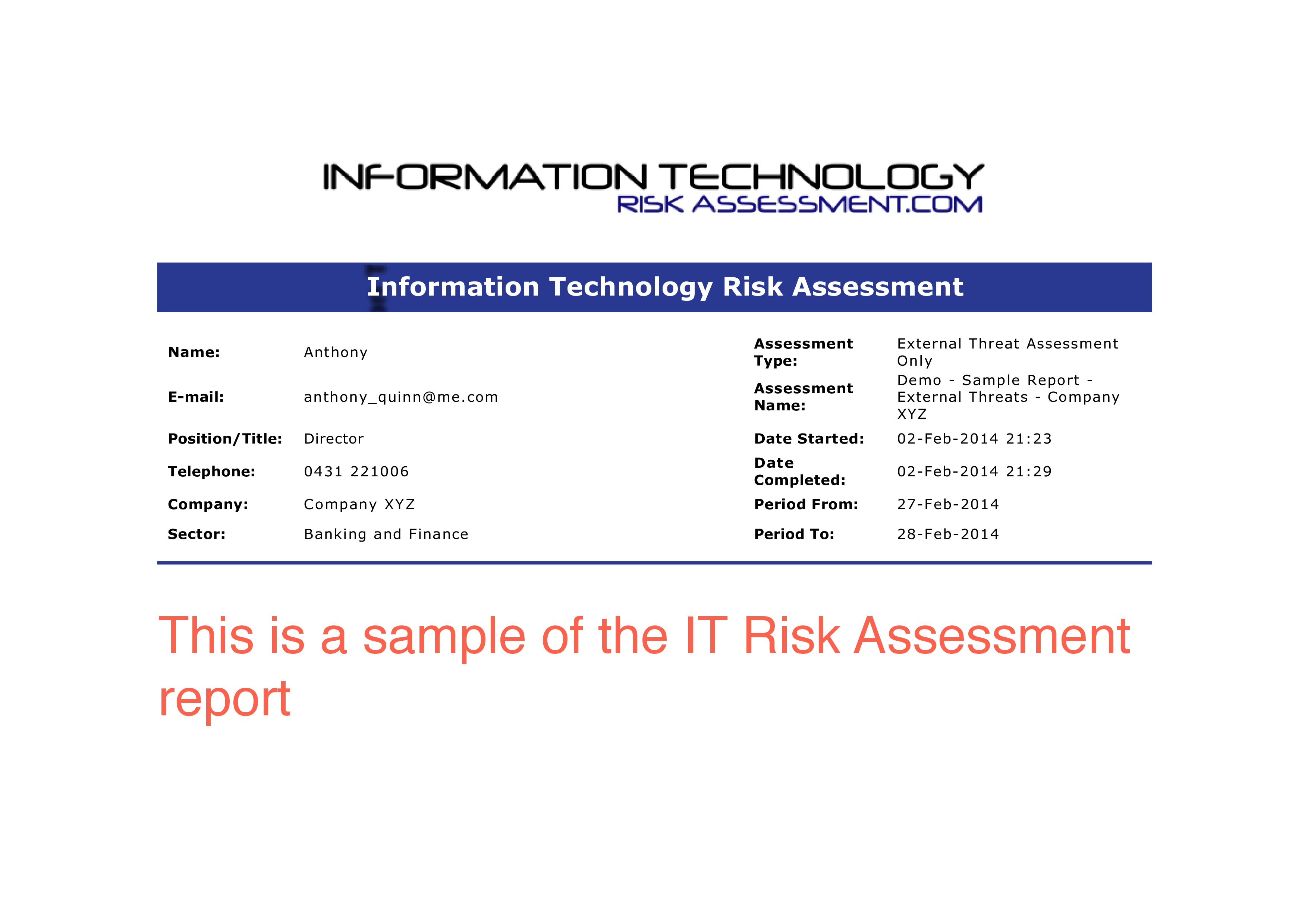
Name: Anthony Assessment Name: Demo - Sample Report - External Threats Company XYZ E-mail: anthonyquinn me.com Assessment Type: Page: 7 of 17 External Threat Assessment Only Date Completed: 02-Feb-2014 21:29 Period From: 27-Feb-2014 Model Assessment Rating Scores Group External Categorization Sub-Categorization Weighting Normalized Maximum Actual Score Score Score 30 30 30 100 8 External Threat Assessment 100 8 External Organisational Level External Operational / Business Process Level External Information / System Level External Technical Threats - Hardware and Software Usage External Technical Threats - Electronic Data Accidental damage, destruction or misuse of data External Technical Threats - Electronic Data Deliberate (Interference) External Technical Threats - Electronic Data Deliberate (Interception) External Technical Threats - Electronic Data Deliberate (Impersonation) External Technical Threats - Electronic Data Deliberate damage, destruction or misuse of data External Physical Threats - Loss from theft, vandalism or sabotage or accidental damage External Physical Threats - Unauthorised access External Physical Threats - Other Environmental Threats - Natural Disasters External Environmental Threats - Other External Support Infrastructure Threats - Power Supply External Support Infrastructure Threats - Telecommunications Name: Anthony E-mail: anthonyquinn me.com Assessment Type: Low Medium High 0 30 0 9 9 9 9 to 19 9 to 19 9 to 19 19 19 19 30 0 9 9 to 19 19 30 0 9 9 to 19 19 30 30 9 9 to 19 19 30 0 9 9 to 19 19 30 0 9 9 to 19 19 30 30 9 9 to 19 19 30 0 9 9 to 19 19 30 30 30 30 30 0 30 30 9 9 9 9 9 9 9 9 19 19 19 19 19 19 19 19 30 30 9 9 to 19 19 30 0 9 9 to 19 19 Assessment Name: Demo - Sample Report - External Threats Company XYZ Page: 8 of 17 External Threat Assessment Only to to to to Date Completed: 02-Feb-2014 21:29 Period From: 27-Feb-2014 External Support Infrastructure Threats - Support Environment Other Threats - Third Party 30 0 9 9 to 19 19
DISCLAIMER
Nothing on this site shall be considered legal advice and no attorney-client relationship is established.
Leave a Reply. If you have any questions or remarks, feel free to post them below.
Related templates
Latest templates
Latest topics
- Excel Templates
Where do I find templates for Excel? How do I create a template in Excel? Check these editable and printable Excel Templates and download them directly! - GDPR Compliance Templates
What do you need to become GDPR compliant? Are you looking for useful GDPR document templates to make you compliant? All these compliance documents will be available to download instantly... - Google Docs Templates
How to create documents in Google Docs? We provide Google Docs compatible template and these are the reasons why it's useful to work with Google Docs... - IT Security Standards Kit
What are IT Security Standards? Check out our collection of this newly updated IT Security Kit Standard templates, including policies, controls, processes, checklists, procedures and other documents. - Letter Format
How to format a letter? Here is a brief overview of common letter formats and templates in USA and UK and get inspirited immediately!
cheese