IT Security Incident Report example
Speichern, ausfüllen, drucken, fertig!
What is the proper way to report a potential information security incident? An easy way to start completing your report is to download this IT Security Incident Report template now!
Verfügbare Gratis-Dateiformate:
.doc- Dieses Dokument wurde von einem Professional zertifiziert
- 100% anpassbar
Business Unternehmen attack Attacke report Berichterstattung Compliance Regelkonformität time Zeit information technology Informationstechnologie Information Incident Vorfall Comments Bemerkungen Information Security Incident Report Bericht über Informationssicherheitsvorfälle Incident Report Template Word Vorfallberichtvorlage Word Incident Report Templates In Vorlagen für Vorfallberichte Incident Report Vorfallsbericht It Security Incident Report IT Sicherheitsbericht It Security Incident Report Sample Beispiel für einen Sicherheitsvorfallsbericht GDPR DSGVO Information Security Informationssicherheit data security Datensicherheit information incident report informational report informational report sample analytical report informational report pdf informational report example for students informational report format informational or analytical reports examples characteristics of informational report what is informational report example what do you write in an information report what are the types of informational reports what are the parts of an informational report informational reports analytical reports differ
How to create an IT Security Incident Report? What is the proper way to report a potential information security incident? An easy way to start completing your report is to download this IT Security Incident Report template now!
We provide this Information Technology Security Incident Report template to help professionalize the way you are working. Our business and legal templates are regularly screened and used by professionals. If time or quality is of the essence, this ready-made template can help you to save time and to focus on the topics that really matter!
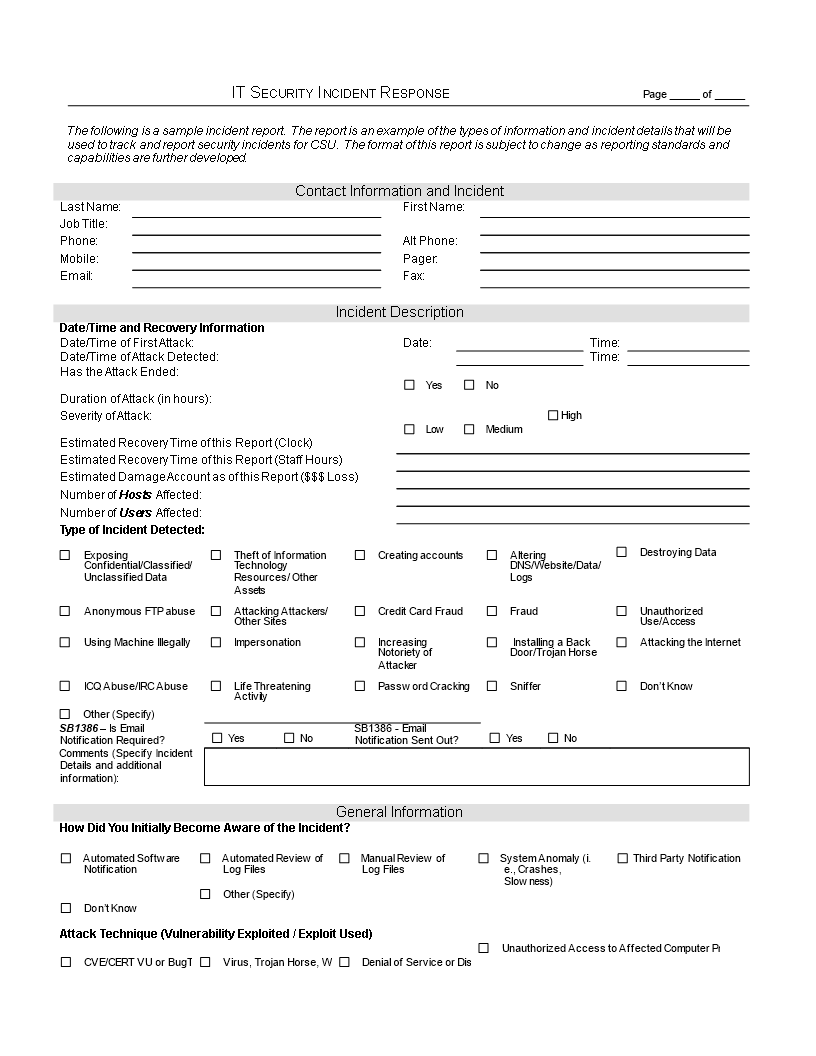
IT Security Incident Report example content:
Crashes, Slowness) Third Party Notification Don t Know Other (Specify) Attack Technique (Vulnerability Exploited / Exploit Used) CVE/CERT VU or BugTraq Number Virus, Trojan Horse, Worm, or Other Malicious Code Denial of Service or Distributed Denial of Service Attack Unauthorized Access to Affected Computer Privileged Compromise (Root/Admin Access) User Account Compromise/Web Compromise (Defacement) Scanning/Probing Other Suspected perpetrator(s) or possible motivation(s) of attack: CSU staff/students/ faculty Former staff/ students/faculty External Party Unknown Other (Specify) Malicious Code Virus, Worm Name or Description of Virus Is Anti-Virus Software Installed on the Affected Computer(s) Yes (Provide Name) No Did the Anti-Virus Software Detect the Virus Yes No When was your Anti-Virus Software Last Updated Network Activity Protocols Name or Description of Virus TCP UDP ICMP IPSec IP Multicast Ipv6 Other Please Identify Source Ports Involved in the Attack: Please Identify Destination Ports Involved in the Attack: Impact of Attack Hosts Individual Hosts Does this Host represent an Attacking or Victim Host Victim Attacker Both Host Name: IP Address: Operating System Affected: Patch Level (if known): Applications Affected: Database: Others: Primary Purpose of this Host: User Desktop Machine User Laptop Machine Web Server Mail Server FTP Server Domain Controller Domain Name Server Time Server NFS/File System Server Database Server Application Server Other Infrastructure Services Bulk Hosts Bulk Host Information (Details): Comments (Please detail incident): Data Compromised: Did the attack result in a loss/compromise of sensitive or personal information Yes (Specify) No Other Comments: Did the attack result in damage to system(s) or date: Yes (Specify) No Other Comments: Law Enforcement Has Law Enforcement Been Notified Yes No Remediation: Please detail what corrective actions have been taken (specify): Comments: Lessons Learned Information (Optional) Did Yo
Nowadays, with the digitalization of our society, the need for data protection became more important. The latest IT Security Standards involve the application of technology to broader social and institutional contexts, and thereby contributes to the servitization of companies, and affects how they compete and interact. This document contains security technology solutions to protect data classified as “Highly Sensitive”, “Sensitive”, “Private” or “Public” as per the Data Classification Standard and Data Handling Guidelines. Specifically:
- Cryptography – Encryption and hashing solutions for protecting sensitive data when in transit or storage, and
- Data Masking – Data masking is a technology for obscuring sensitive information in non-production environments. Through data masking [Company Name] protects the content of sensitive data in non-production environments to ensure that:
- Application developers, testers, privileged users and outsourcing vendors do not have unauthorized access to such information.
- The data maintains the referential integrity of the original production data.
Using this Information Technology Security Incident Report template guarantees you will save time, cost and efforts! Completing documents has never been easier!
Download this IT Security Incident Report template now for your own benefit!
HAFTUNGSAUSSCHLUSS
Nichts auf dieser Website gilt als Rechtsberatung und kein Mandatsverhältnis wird hergestellt.
Wenn Sie Fragen oder Anmerkungen haben, können Sie sie gerne unten veröffentlichen.

