IT Security Roadmap
Sponsored Link免费模板 保存,填空,打印,三步搞定!
Download IT Security Roadmap
微软电子表格 (.xlsx)- 本文档已通过专业认证
- 100%可定制
- 这是一个数字下载 (569.94 kB)
- 语: English
Sponsored Link
How to implement CyberSecurity in a business? What are the ways to implement cyber security? Download this IT Security Roadmap if you are working on IEC, NIST, ISO27001:2013 or other IT and CyberSecurity Standards and control objectives.
Appropriate data security controls reduce the likelihood (and impact) of data breach incidents during various phases of the data lifecycle. The purpose of this standard is to set out the rules for securing the companies' data during transmission and storage. This document provides best practice recommendations on information security management for use by those responsible for initiating, implementing or maintaining information security management systems (ISMS).
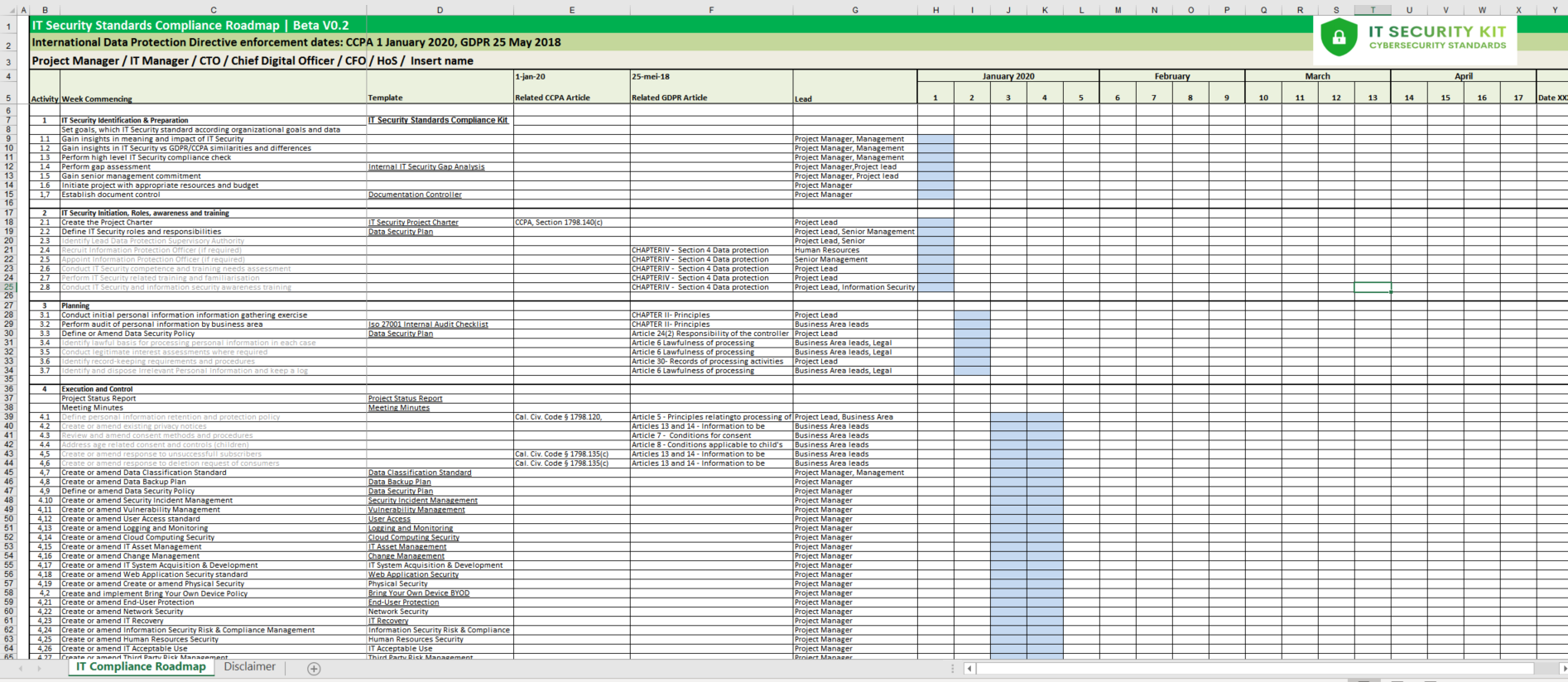
The following activities are possible in order to implement an IT security system for your organization, including GDPR and/or CCPA related activities:
IT Security Identification & Preparation
IT Security Initiation, Roles, awareness and training
Planning
Execution and Control
Data subject management
Controllers and processor
Data protection impact assessment
International transfers
Personal information breach management
Project closure
- Set goals, which IT Security standard according organizational goals and data security
- Gain insights in the meaning and impact of IT Security
- Gain insights in IT Security vs GDPR/CCPA similarities and differences
- Perform high-level IT Security compliance check
- Perform gap assessment
- Gain senior management commitment
- Initiate a project with appropriate resources and budget
- Establish document control
IT Security Initiation, Roles, awareness and training
- Create the Project Charter
- Define IT security roles and responsibilities
- Identify Lead Data Protection Supervisory Authority
- Recruit Information Protection Officer (if required)
- Appoint Information Protection Officer (if required)
- Conduct IT security competence and training needs assessment
- Perform IT security-related training and familiarisation
- Conduct IT security and information security awareness training
Planning
- Conduct initial personal information gathering exercise
- Perform audit of personal information by business area
- Define or Amend Data Security Policy
- Identify a lawful basis for processing personal information in each case
- Conduct legitimate interest assessments where required
- Identify record-keeping requirements and procedures
- Identify and dispose of Irrelevant Personal Information and keep a log
Execution and Control
- Project Status Report
- Meeting Minutes
- Define personal information retention and protection policy
- Create or amend existing privacy notices
- Review and amend consent methods and procedures
- Address age-related consent and controls (children)
- Create or amend response to unsuccessful subscribers
- Create or amend response to deletion request of consumers
- Create or amend Data Classification Standard
- Create or amend Data Backup Plan
- Define or amend Data Security Policy
- Create or amend Security Incident Management
- Create or amend Vulnerability Management
- Create or amend User Access standard
- Create or amend Logging and Monitoring
- Create or amend Cloud Computing Security
- Create or amend IT Asset Management
- Create or amend Change Management
- Create or amend IT System Acquisition & Development
- Create or amend Web Application Security standard
- Create or amend Create or amend Physical Security
- Create or amend End-User Protection
- Create or amend Network Security
- Create or amend IT Recovery
- Create or amend Information Security Risk & Compliance Management
- Create or amend Human Resources Security
- Create or amend IT Acceptable Use
- Create or amend Third-Party Risk Management
- Secure Algorithm List
Data subject management
- Create and implement data subject request procedures
- Create and implement data subject consent withdrawal form
- Create and implement parental consent withdrawal form
- Start recording data subject requests
- Create and implement User Deletion Request Policy
- Create and implement Data Subject Access Request Form
Controllers and processor
- Update contracts with processors to be IT Security compliant
- Distribute supplier questionnaires regarding personal information protection
- Provide information to controllers for whom we act as a processor
- Update contracts with controllers to be IT Security compliant
- Address employee confidentiality requirements
- Create and implement Bring Your Own Device Policy
Data protection impact assessment
- Define the data protection impact assessment process
- Conduct data protection impact assessment training
- Perform initial data protection impact assessment
International transfers
- Identify international transfers of personal information
- Assess the legality of existing international transfers
- Put in place agreements for international transfers of personal information (where required)
Personal information breach management
- Create information security incident management procedure
- Create information security incident management register
- Create personal information breach notification procedure (Data Subjects)
- Create personal information breach notification procedure (Supervisory Authority)
- Conduct information security incident management training
- Test incident management and breach notification procedures
- Create a business continuity plan or disaster plan in case of crisis
- Inform the data subjects that were exposed to a data breach
Project closure
- Repeat gap assessment to identify remaining non-compliant areas
- Respond to complaints of data privacy breaches, etc
- Address any remaining non-compliant areas
- Perform post-project review
Nowadays, with the digitalization of our society, the need for data protection became more important. The latest IT Security Standards involve the application of technology to broader social and institutional contexts, and thereby contributes to the servitization of companies, and affects how they compete and interact. This document contains security technology solutions to protect data classified as “Highly Sensitive”, “Sensitive”, “Private” or “Public” as per the Data Classification Standard and Data Handling Guidelines. Specifically:
- Cryptography – Encryption and hashing solutions for protecting sensitive data when in transit or storage, and
- Data Masking – Data masking is a technology for obscuring sensitive information in non-production environments. Through data masking [Company Name] protects the content of sensitive data in non-production environments to ensure that:
- Application developers, testers, privileged users, and outsourcing vendors do not have unauthorized access to such information.
- The data maintains the referential integrity of the original production data.
Download this IT Security Roadmap now. Besides this document, make sure to have a look at this fit-for-purpose IT Security Kit here with over 40 useful templates. The document(s) are easy to modify and can be downloaded directly after purchase.
DISCLAIMER
Nothing on this site shall be considered legal advice and no attorney-client relationship is established.
发表评论。 如果您有任何问题或意见,请随时在下面发布
相关文件
Sponsored Link